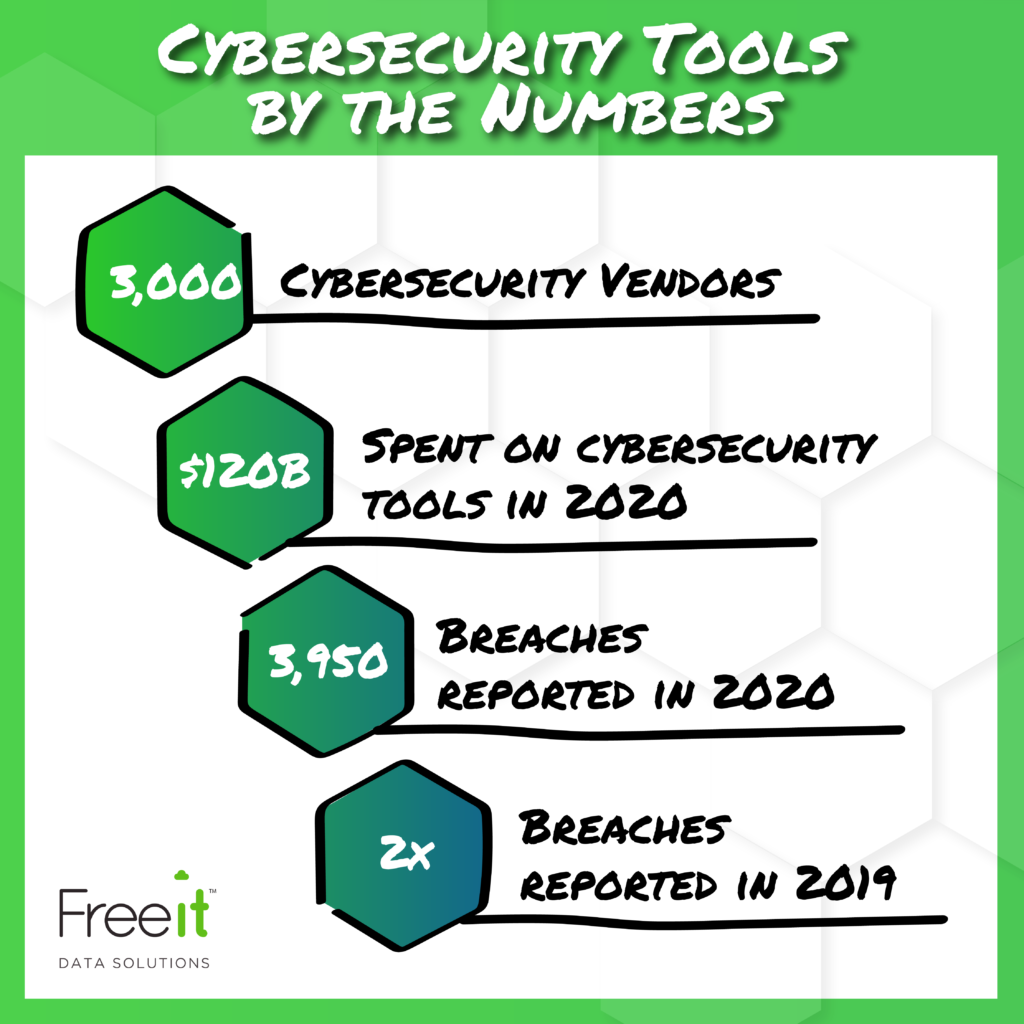
“3,000. That’s the number of cybersecurity vendors there are in the world selling tools to stop cyber crime. $120 billion. That’s the amount of money that we spent in 2020 on those 3,000 vendors buying our tools to stop cyber crime. However, even though we’re spending all this money on all these tools, there were still 3,950 reported breaches last year, which was a double from the year before. Cybersecurity does not have a tools problem. Cybersecurity has a tools effectiveness problem. Cybersecurity has an operational problem.”
Jim Johnson, Arctic Wolf
What are the biggest struggles that security teams are dealing with right now?
- There’s not enough time to sift through and prioritize all of the alerts and events that are generated by cybersecurity tools, which means that teams waste time looking at things that aren’t important. Alternatively, if all alerts are just going into some bucket that nobody has the time to look at, you’re probably missing threats.
- There’s not an overarching security strategy so you know where the risk is and how it should be addressed. The most common scenario is that a critical incident like a breach or known vulnerability comes out and the organization buys a specific tool to fix that problem. But, later you realize that additional resources are required to operate the new tool effectively, in addition to continuing to balance everything else. Without a holistic security strategy, you’re wasting money on tools that might not be addressing the real problem.
- It’s not “if” you’re going to get breached, it’s “when” you’re going to get breached or hit with ransomware. What is your maximum tolerable downtime? What is the amount of time that you don’t have access to your data or your assets, before it’s crippling to your business? And how long will it take before you detect that breach and respond to it? The revenue impacts from fines, reputation damage, and operational interruptions are only the beginning.
How do we solve these challenges with cybersecurity tools?
- Prioritize your alerts. Determine the top two to five things that you really, really need to monitor, and then you will not only save time, but you will use your resources more effectively.
- Demonstrate a comprehensive security posture. Develop a reporting structure that allows you to quickly inform auditors and business leaders without having to use multiple tools and build a custom report every time.
- Document your compliance framework. Develop risk level identification, proactive mitigation efforts, compliance processes, and alignment between security posture and organizational goals.
- Optimize and maintain your tool sets. Keep up with patches and ensure consistent configuration and implementation.
What do you need to get there?
- The ability to see everything. It doesn’t matter if you subscribe to SANS or NIST, or any one of the other security frameworks, the first tenant is being able to see everything in the environment and what’s running on it.
- The capability to filter alerts. In order to get from alert fatigue to accurately prioritized notifications, they must be defined and allocated appropriately.
- A proactive approach. There are always threats, but you need to be sure to look at the entire environment, identify gaps and other areas of concern, and implement a plan to tackle them.
- Security experts. Every organization needs people that understand security and how to address it holistically, so you can ensure the organization is protected. Whether these are internal resources or external partners, make sure that someone is the designated responsible party.
See the rest of this webinar on-demand. Watch now.