What is Security?
It used to be that keeping your business “secure” meant making sure the doors were locked at night or maybe there was a security guard on the premises. Now, in many instances, the physical assets of a business are only a fraction of the value that needs to be protected. The majority of business value is now in ones and zeros, bits and bytes, megabytes, gigabytes, terabytes and more. It’s in the ownership and control of data – whether financial, medical, or personal.
With the overwhelming frequency of data theft, ransomware, cyberattacks, and more – the challenges of security are becoming ever more complex and must prioritize the protection of digital assets. Security can’t just be a fancy deadbolt or even a complex password, it has to become an all-encompassing framework so that business value can be retained.
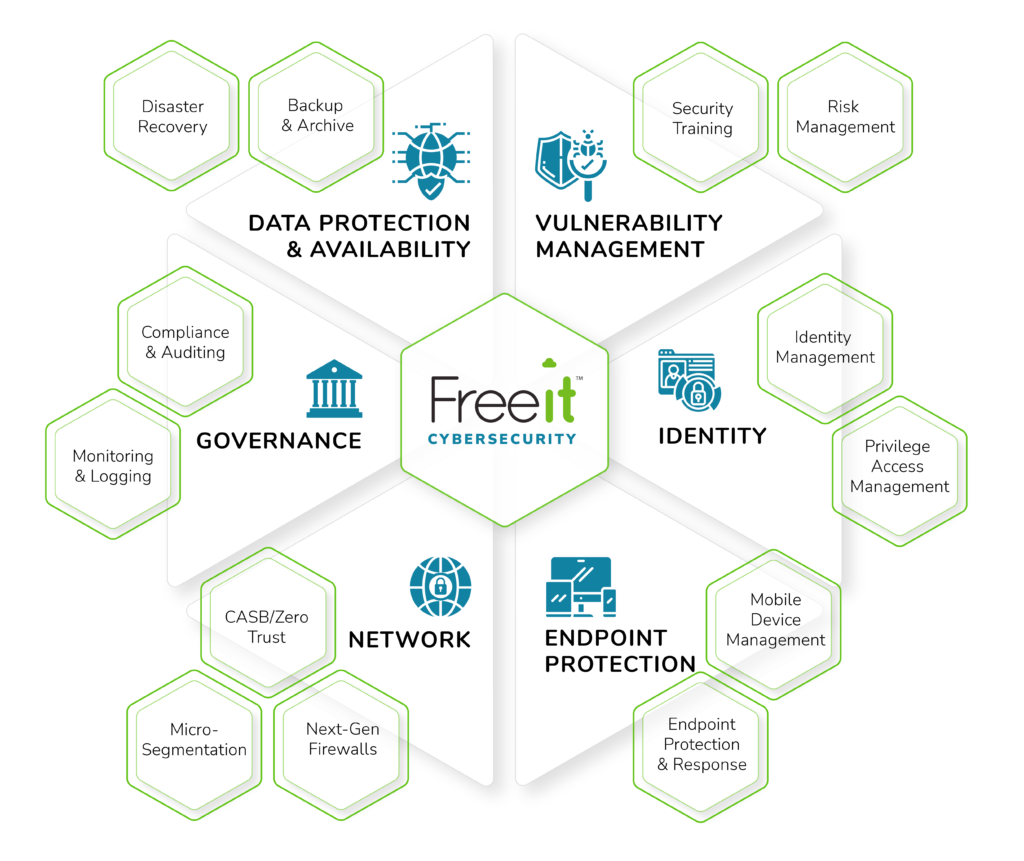
Security Framework
Your organization faces a myriad of cybersecurity threats on a regular basis. Each layer of your defense must interconnect. That way, you can create a well-rounded strategy that provides layered protection throughout the entire organization. As you consider your security framework, what are some of the areas where focus should be prioritized? Just a few crucial considerations are:
- Data Governance and Compliance
- Data Protection and Availability
- Network Architecture
- Identity and Access Control
- Endpoint Protection
- Vulnerability Management
Let’s take a quick look at each of these and why they are important. In the coming weeks, we will do a deeper dive into some of the best ways to address each of them.
Data Governance and Compliance
Not only is the amount of data that businesses manage increasing exponentially, the regulations that govern the treatment of data are also increasing in complexity. Technology is changing at an astronomical rate, creating ever more opportunities for connections, transactions, and monetization of information. Without extremely careful attention, an organization could incur significant costs from lawsuits or fines if they fail to comply with applicable regulations.
Data Protection and Availability
These two things go together in the security framework because your organization needs data to be available for decision-making and business optimization. However, it is important to be deliberate in determining which data is available, when, and to whom. These factors will affect how data is accessed and protected. Because data is inherently valuable, it also must be protected from external threats.
As ransomware becomes part of the daily cybersecurity and risk conversations in a growing number of industries, preventing ransomware attacks must become a larger focus of security efforts. In addition, a recovery plan to address how your business will respond and move forward in worst-case scenarios is an important component of your security framework. Failure to protect data can have serious, long-term financial consequences for the business, whether as a result of a costly data breach by a malicious cyber attacker, or through loss of reputation, and reduced ability to compete in data-driven industries.
Network Architecture
Network architecture has a huge impact on the way that all components of network security are addressed. A comprehensive understanding of how network components are connected and when, how, and where data is accessed is required in order to develop effective protection measures.
Many organizations are implementing a Zero Trust model that is based on the concept that organizations should not automatically trust anything inside or outside its perimeters and instead must verify everything trying to connect to its systems before granting access. As networks become increasingly complex, the implemented security solutions must also become more sophisticated.
Identity and Access Control
A comprehensive access control approach dictates that all users, whether inside or outside of the organization’s network, must be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data.
Access control measures give users access to the resources that they need, while preventing them from accessing systems or tools that are unauthorized. As you can imagine, knowing and keeping track of these permissions is vital to ensuring data security. Malicious cyberattacks frequently happen when credentials are misused, and the ability to quickly adjust user access is an important component of a layered security approach.
Endpoint Protection
The number and types of devices connected to enterprise networks has ballooned, especially as a result of bring-your-own-device (BYOD) policies and the Internet of Things (IoT). Each device is now a potential point of vulnerability, Endpoint protection has evolved from basic antivirus software to more comprehensive tools able to quickly detect, analyze, block, and contain attacks in progress. By creating and enforcing rules for endpoints, endpoint protection solutions are able to identify sensitive data and encrypt it, or block the copying or transfer of certain files or sensitive data based on enterprise classification.
Understanding the volume and types of endpoints in your network has a significant impact on how endpoint protection can be implemented.
Vulnerability Management
Every time you add a new affiliate partner, client, customer or employee your organization is exposed to new threats. Protecting your organization from these threats requires an adaptable vulnerability management solution.
Not only is your organization’s “attack surface” constantly changing, as you add new mobile devices, cloud services, networks, and applications to your environments, threats and attackers are also constantly changing. With every change comes new risks that must be identified and addressed.
Unfortunately, many organizations are susceptible to cyberattacks as a result of human error. Because of this, security training and awareness are other key areas to address. The inability to recognize spam or phishing emails, and the constant changing of security protocols can leave your organization vulnerable. A strong authentication solution and regular employee training can reduce these risks.
The vulnerability management process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them enables organizations to prioritize possible threats and minimize their “attack surface.”
This prioritization is required to allocate resources according to risk-management or risk-reduction urgency. In times where resource constraints are the norm, prioritization and vulnerability management are now an integral part of your security framework.
Closing
The good news is that there are dozens upon dozens of companies and tools or solutions to help with each of these security challenges. The bad news is that there are hundreds or thousands of companies and tools or solutions for cybersecurity, and it’s extremely complicated to determine which set of options is the best fit for your organization’s needs. Have you ever tried to draw a Venn Diagram with 100 circles?
Or, even more to the point – what does the Venn Diagram of your company’s needs look like just for these 6 areas?
The Freeit experts can work with you to develop and implement a layered security strategy.
Together, we can ensure that your IT infrastructure is protected from threats while improving your security posture and maintaining compliance.